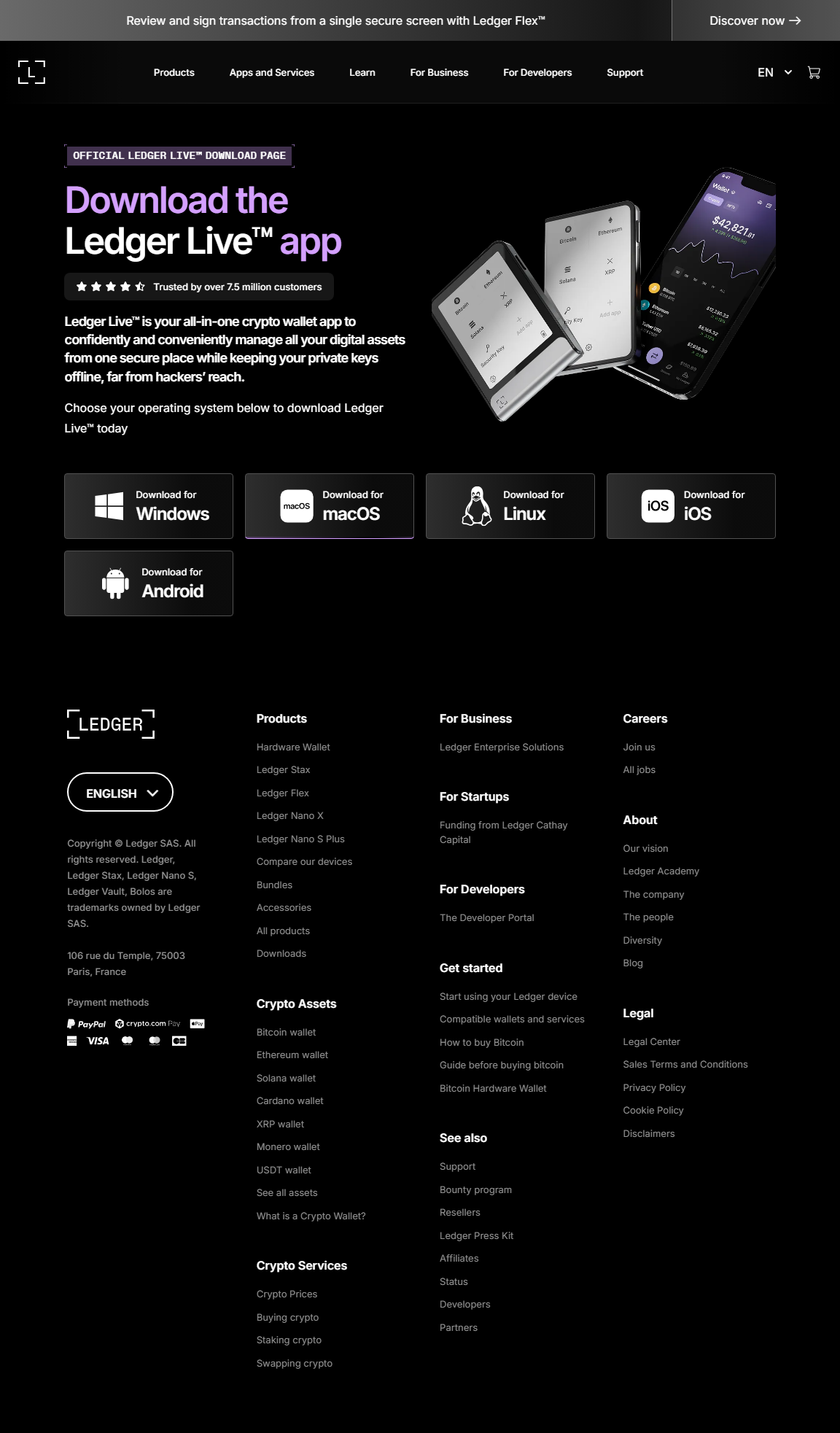
Ledger Login
A complete 2025 guide explaining how Ledger login works, why it’s different from traditional sign-ins,
and how to safely authenticate your hardware wallet using Ledger Live.
Unlike typical websites or crypto exchanges, Ledger login does not involve usernames, passwords, or cloud accounts.
Instead, your Ledger hardware wallet acts as the login itself — a physical cryptographic key that verifies your identity every time you interact with your assets.
The process revolves around a secure handshake between Ledger Live and your physical Ledger device.
Because private keys never leave the hardware wallet, this approach protects you from phishing, malware attacks, SIM swaps, and remote hacking attempts that plague online wallets.
⚠️ Critical Ledger Login Reminder
Ledger will **never** require your 24-word recovery phrase to log in.
Entering your phrase anywhere except the physical Ledger device itself is a scam.
What Does “Ledger Login” Mean?
Ledger login is the process of verifying ownership of your crypto wallet by physically connecting your Ledger device and approving actions on its secure screen.
This ensures your identity and your crypto ownership cannot be faked or stolen by remote attackers.
✔ Your Ledger device acts as your authentication key
✔ Ledger Live checks your device’s authenticity
✔ You approve requests physically on the screen
✔ Transactions cannot be authorized without your device
“With a Ledger device, the login is something you *hold*, not something you *remember*.”
Hardware-secured identity is the future of crypto protection.
How Ledger Login Works — Step by Step
Here is the complete, secure login workflow:
1. Launch Ledger Live
Always use the official version — bookmarked or manually typed URLs reduce phishing risks.
2. Connect Your Ledger Device
Use USB-C for Nano S Plus and USB-C/Bluetooth for Nano X.
3. Enter Your PIN (On Device Only)
This unlocks the secure element chip. The PIN is never shared with Ledger Live.
4. Open the Required App
Ledger Live may ask you to open the Bitcoin, Ethereum, or specific blockchain app.
5. Approve the Authentication Request
Your device verifies Ledger Live’s authenticity using cryptographic signatures.
Ledger Login vs Exchange Login
| Aspect | Ledger Login | Exchange Login |
|---|---|---|
| Password Required | No | Yes |
| Private Key Exposure | Impossible | Possible |
| Ownership Model | Self-custody | Custodial |
| Phishing Risk | Very Low | High |
Best Practices for Secure Ledger Login
- Use only the official Ledger Live app — avoid browser-based clones.
- Never enter your recovery phrase on any digital device.
- Verify all transaction details on the device’s physical screen.
- Enable a password lock inside Ledger Live for added protection.
- Keep your Ledger firmware updated via Ledger Live.
FAQ — Ledger Login
Does Ledger have a traditional login page?
No. Authentication happens only through your physical device and Ledger Live.
No. Authentication happens only through your physical device and Ledger Live.
Can I access my Ledger wallet without the device?
No — the device is mandatory for all secure actions.
No — the device is mandatory for all secure actions.
Is the PIN part of the login?
Yes. Your PIN unlocks your Ledger but is never transmitted to Ledger Live.
Yes. Your PIN unlocks your Ledger but is never transmitted to Ledger Live.
Can someone hack my Ledger login remotely?
No. Without your physical device *and* PIN, access is impossible.
No. Without your physical device *and* PIN, access is impossible.
Ledger Login — Security Reinvented
With Ledger login, your crypto protection begins at the hardware level.
No cloud accounts, no passwords, no digital vulnerabilities — just pure, verifiable ownership.
Choose Ledger login to ensure your digital wealth stays safe, offline, and fully under your control.